
The demise of the humble password may be upon us! Research and development in the field of quantum computing could bring about a significant change in how user credentials are effectively secured.
However, the field has some way to go before it sees widespread use. For now, the password remains a key factor utilised by organisations to protect a user’s access to corporate and personal information. Recent, high-profile cyber attacks have once again demonstrated the vulnerability of poorly implemented password policy and inadequate awareness of how best to use passwords to protect our information. What can we do to ensure that our use of passwords is as effective as possible? How can we make life difficult for those who would steal our secrets?
Fortify your password
Password strength is not just about complexity. Most of us are familiar with the requirements frequently enforced by our IT administrators. Ensuring that our passwords contain a mixture of uppercase, lowercase, numerals and special characters is beneficial in our aim to make life difficult for the “bad guys”. The next step that we can take is to increase the length of our passwords. As technology progresses and passwords become more vulnerable to cracking, the length of the password becomes increasingly important. As an example, the Payment Card Industry Data Security Standard (PCI DSS) now requires 12-character passwords in a world where most companies are still requiring only 7 to 8. Human nature is such that without robust awareness training most users will use the minimum required.
Research by Hive has demonstrated just how important password length is in foiling brute force attacks and this message should be a key component of cyber security awareness training. It is also an important lesson for people when they are constructing their passwords for personal use such as for online banking and shopping. You may not be able to prevent the theft of your password from a retailer, but you can make it as difficult as possible for criminals when they seek to offline brute force your stolen credentials.
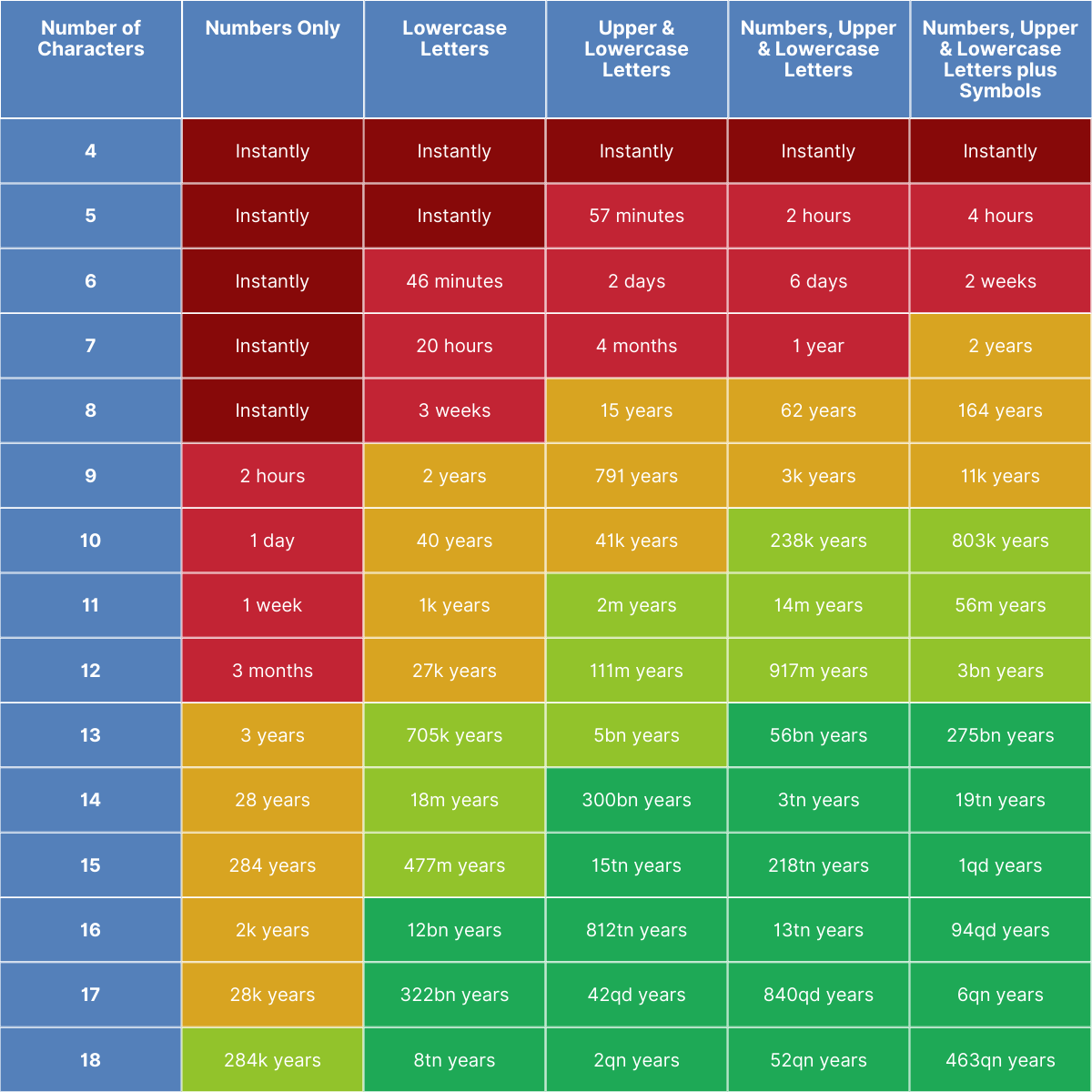
Including phrases in your password
A question that is frequently asked by users when we are encouraging them to increase the length of their already complex passwords is “how am I supposed to remember that without writing it down?”. This is a valid question. Unless we are using a secure password vault, we are asking users to remember an increasingly long and complex password, which is a real challenge. So, how can we make life easier? The trick here lies in the use of phrases which assist in remembering the password.
As an example, by taking the first character from the following phrase we can build a password that is unique to us.
"I am going to go with friends to Ibiza on holiday next year"
This creates: IagtgwftIohny
By substituting some characters, we can create a complex 13-character password:
I@gtgwftI0hny
This password is not the most complex that we could create but it contains all the usual complexity requirements, is sufficiently long that it is very difficult to crack and it is unique to us.
Things to keep in mind:
- Do not use words within the password
- Do not use three or more identical characters in sequence
- Try to use multiple special characters where possible
- When prompted to change your password do not simply change a single character (often a user will use the same password whilst just changing 1,2,3 etc at the end). Instead create a whole new prompt phase. It is better to be safe.
Using “secret questions”
Most of us are familiar with the practice of organisations asking us to provide answers to several questions. These are used to validate our identity if we need to make account changes such as changing our password. These questions are often very standard and include questions like:
- “What is your mother’s maiden name?”
- “Which secondary school did you attend?”
- “What is the father’s middle name?"
The core issue with the use of these questions is that most people answer them truthfully. Unfortunately, it is now not all that difficult to research the answers to these questions due to the proliferation of information that exists about us online through social media pages and websites such as those associated with genealogy.
Over time, cyber-criminals have used social media to gather personal information through social engineering tactics. Posts such as this ask seemingly innocent questions, such as “Your Hollywood alter ego is your first pet’s name+ your mother’s maiden name!” act as tools to draw the answer to security questions from the user. It’s a subtle but effective way for attackers to collect sensitive data and potentially gain access to personal accounts.
It is far safer to lie when responding to security questions. You cannot change the question, but you can determine the answer. One option worth considering is to respond with something that only you will know but you are reminded of the answer by the question. As an example, for the question “Which secondary school did you attend?” you could create an association with your favourite subject so the response would be something like “Physics”. It is all about making it tougher for criminals to steal our possessions.
Future technology development will likely spell the demise of manually entered authentication factors such as passwords. Until that happens, we, as users, need to do as much as we can to protect our, and our employers, information.
At Talan, our Cybersecurity team is committed to strengthening businesses cyber defences. Contact us today to see how we help your cyber strategy, operations and compliance ambitions.
Contact us

